CatLogs – Advanced HTTP Based Stealer|RAT|Ransomware|Clipper|Keylogger
Introduction:
In today’s ever-evolving landscape of cybersecurity, where technology advances rapidly, so do the tactics of malicious actors aiming to compromise data, privacy, and network security. One menacing threat that has recently come into the spotlight is CatLogs – an HTTP-based virus with the potential to wreak havoc for online users. In this article, we’ll embark on a comprehensive journey into the world of CatLogs, uncovering its origins, operational methods, and strategies for prevention and mitigation.
Unmasking CatLogs:
CatLogs represents a relatively new breed of malware, harnessing the power of the Hypertext Transfer Protocol (HTTP) to distribute and execute malicious code on targeted devices. While HTTP stands as a ubiquitous protocol for transmitting data over the internet, CatLogs capitalizes on its vulnerabilities to infiltrate systems, compromise user data, and often serve as a gateway for further cyberattacks. The moniker “CatLogs” aptly describes its capacity to stealthily log user activities, akin to a cat silently stalking its prey.
Operational Approach:
- Infection Strategy: CatLogs typically gains access to a user’s device through deceitful means, such as phishing emails, contaminated downloads, or compromised websites. Once a user unwittingly interacts with the tainted content, the malware seizes an opportunity to infiltrate the system.
- Communication with Command and Control (C2) Servers: CatLogs establishes a connection with remote C2 servers by leveraging HTTP requests. These servers act as a central control hub for the malware’s operators, granting them the power to issue commands and extract sensitive data.
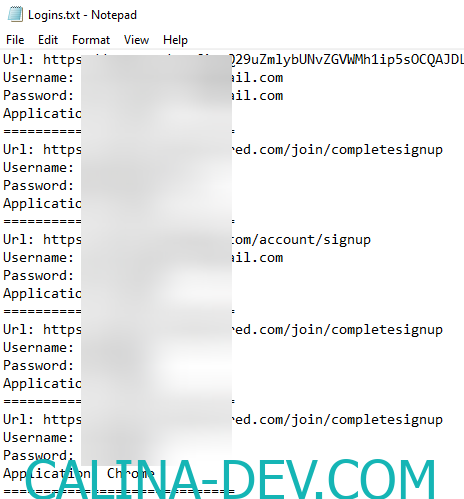
- Data Harvesting: Once nestled within the victim’s system, CatLogs commences its malicious operations. It diligently collects a plethora of information, including keystrokes, login credentials, personal data, and browsing history – all while remaining undetected by the user.
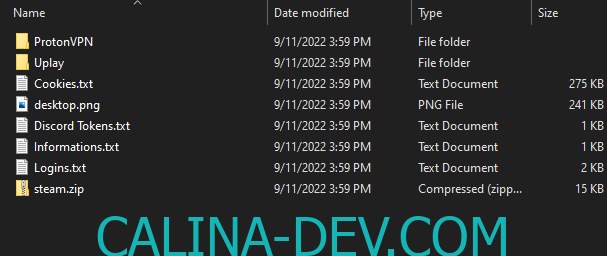
- Data Exfiltration: CatLogs consistently dispatches the stolen data to C2 servers via encrypted HTTP requests, thwarting detection by security measures.
- Payload Delivery: On certain occasions, CatLogs functions as a delivery mechanism for additional malware or ransomware, further imperiling the victim’s system.
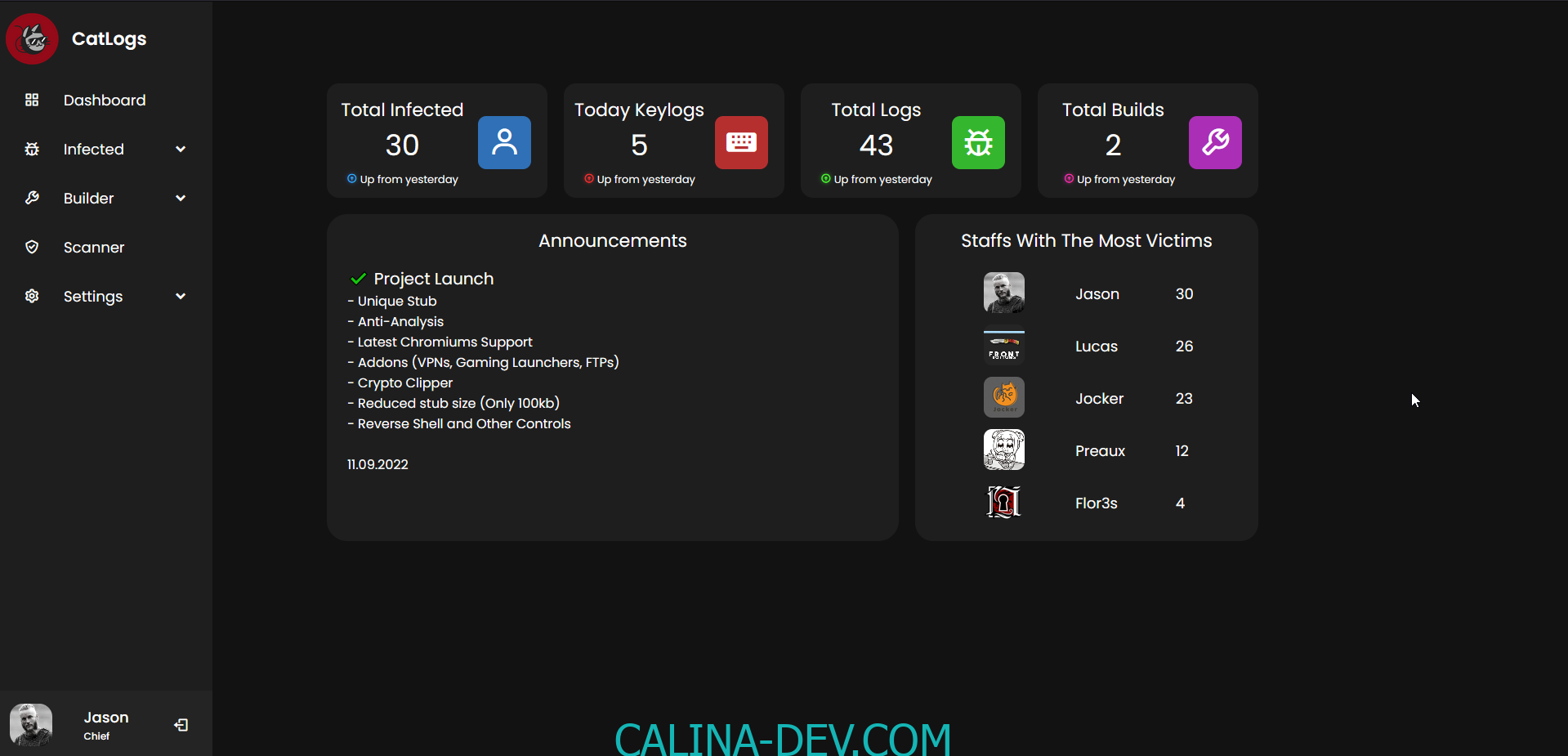
CatLogs Features:
- Browser Logins and Cookies Theft
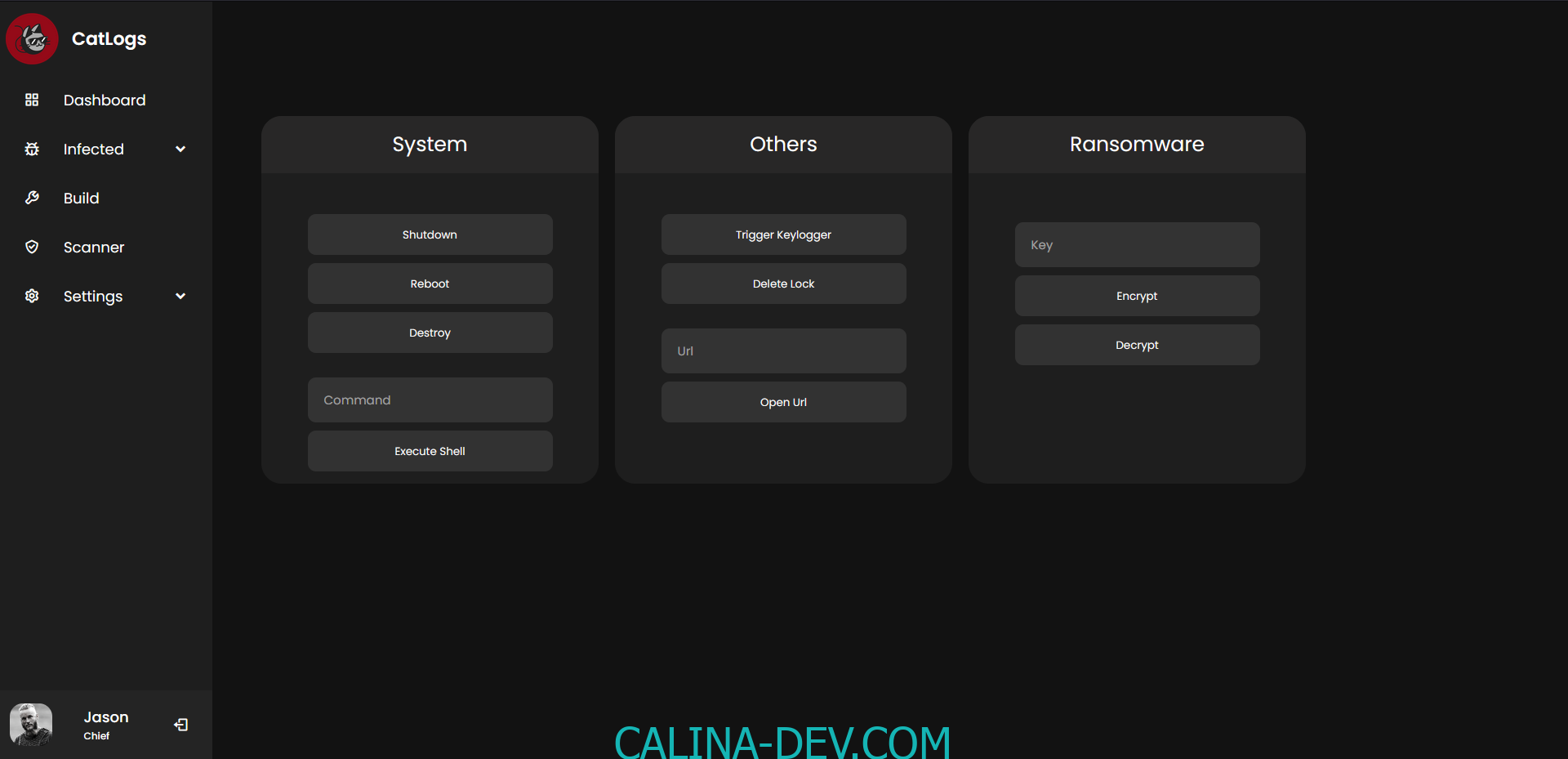
- Ransomware Functions (Custom Key Encryption/Decryption)
- RAT Capability (Shell/System Commands)
- Clipper for Cryptocurrency (BTC/ETH)
- System Information Gathering
- Keylogger Functionality
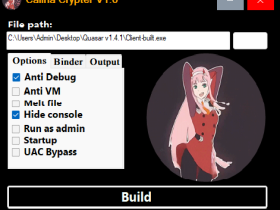
- Anti-Analysis Measures (Sandboxie, Virtual Machines, HoneyPots)
- Recovery of VPNs, Gaming Launchers, VOIP Clients
- Compact 91KB Payload Stub
- User-Friendly Setup and Launch
- Compatible with CashCrypters supporting .NET (4.6) Payloads
- Disabling of Host System’s AVs recommended for optimal functionality
Conclusion:
In the realm of cybersecurity, staying one step ahead of the ever-adapting threats is crucial. CatLogs represents a significant challenge, given its clever utilization of HTTP for nefarious purposes. To safeguard against this menacing threat, it’s essential for individuals, businesses, and organizations to remain vigilant and implement robust security measures. Awareness and proactive defenses are key in the ongoing battle against CatLogs and similar emerging threats.
WE OFFER INSTALL ANY HACKTOOL AT CHEAP PRICES PLEASE CONTACT @calinadev
PASSWORD : calina-dev.com
DOWNLOAD SOON
We Love Cricket
We Love Cricket








Leave a Reply