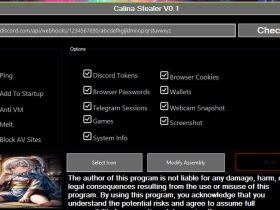
Redline Botnet boasts powerful features and is known for its capabilities in the realm of stealers. This botnet offers a wide array of features, making it a prominent choice among cybercriminals. It has gained popularity for its ability to facilitate various malicious activities, including unauthorized access to accounts, theft of cookies, credit card data, cryptocurrency wallets, and more. Redline Botnet has even become a preferred tool for hackers, and when combined with tools like cookies checkers, it enhances their capabilities significantly.
Introduction
The realm of cybersecurity is in a constant state of flux, with new threats emerging regularly. One such perilous adversary that has garnered significant attention in recent times is the RedLine Stealer. RedLine’s prowess goes beyond mere anti-detection and anti-analysis tricks, delving deep into reconnaissance of its operating environment, ensuring a comprehensive understanding of the host system. In this article, we will delve into the intricacies of RedLine Data Stealer, examining its capabilities and the data it seeks to pilfer.
Understanding RedLine’s Reconnaissance
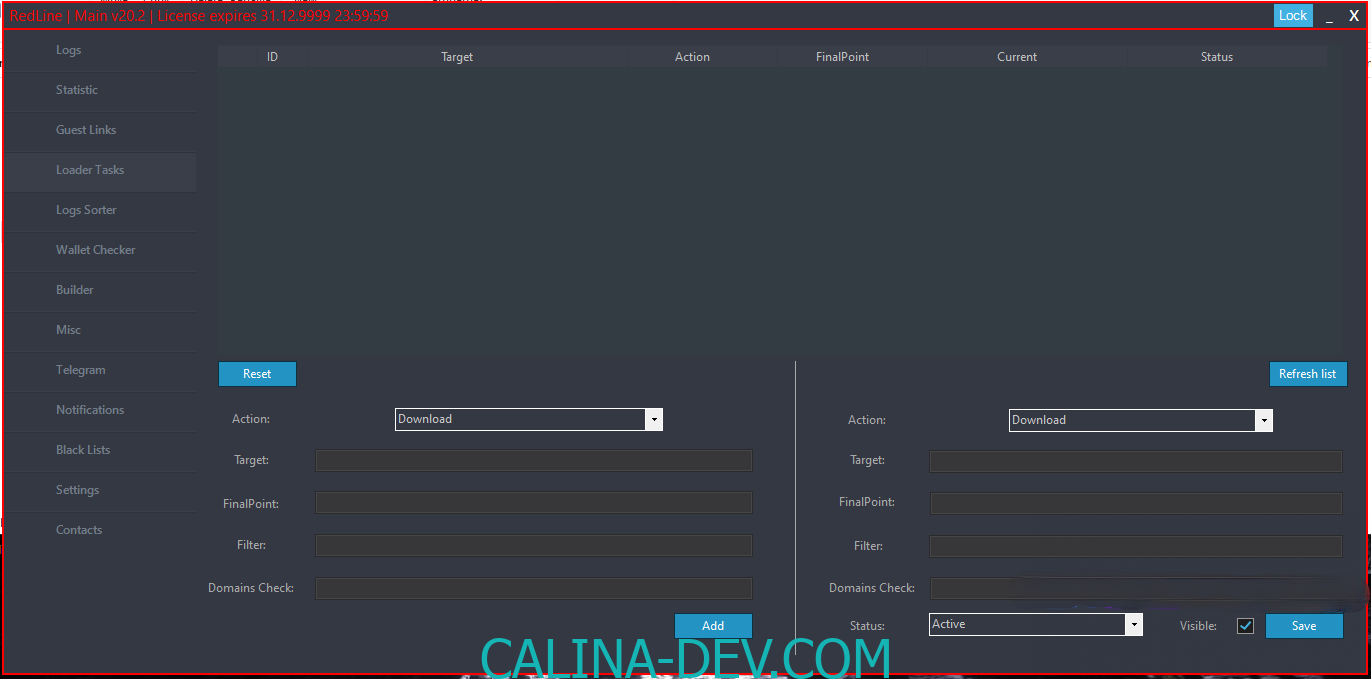
RedLine’s initial reconnaissance extends to a range of critical system attributes, even when provided with a blank configuration from the Command and Control (C2) server. These include:
- Time Zone
- Language Settings
- Hardware Information
- Usernames
- Windows Version and Build
- Screenshots
- Installed Browsers
- Installed Antivirus Software
- Currently Running Processes
However, with the right configurations in place, RedLine Stealer can expand its data-gathering capabilities significantly. It can pilfer a wide range of sensitive information, including passwords of various categories, bank card numbers, cryptocurrency wallets, and data from web browsers and specific desktop applications.
Exploring RedLine’s Data Sources
- Web Browsers:
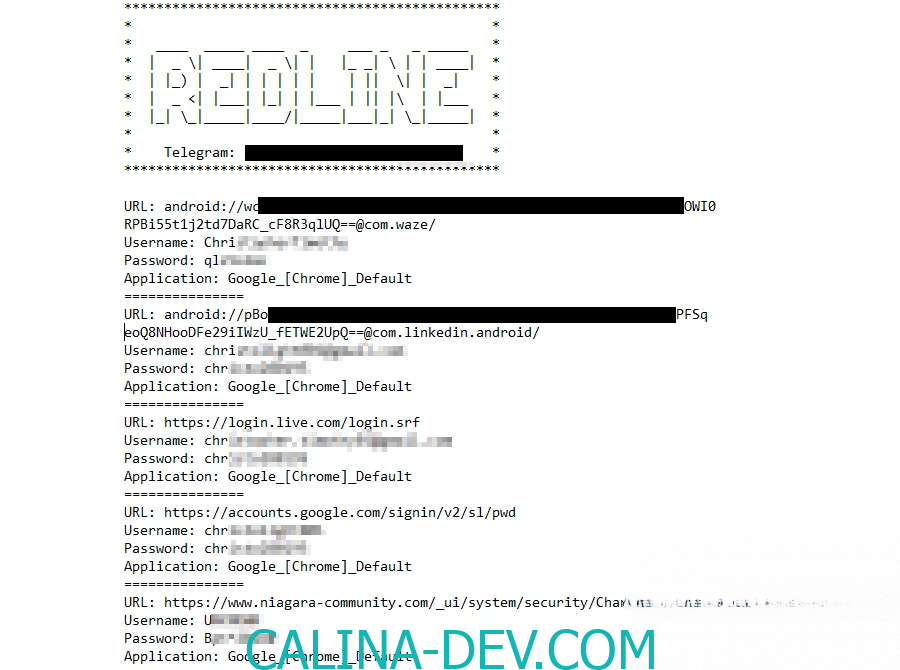
RedLine Stealer can infiltrate numerous web browsers, encompassing popular choices such as Chrome, Opera, Firefox, and Chromium-based alternatives. Within these browsers, it focuses on two key categories of data:
a. In-browser data: This includes saved passwords and credit card information obtained from AutoFill forms.
b. Cryptocurrency wallet data from browser add-ons: RedLine targets extensions related to cryptocurrency wallets and retrieves relevant information, including passwords and cookies. The method of extracting these data depends on how the browser stores cookies, either as encrypted files or within an SQL database.
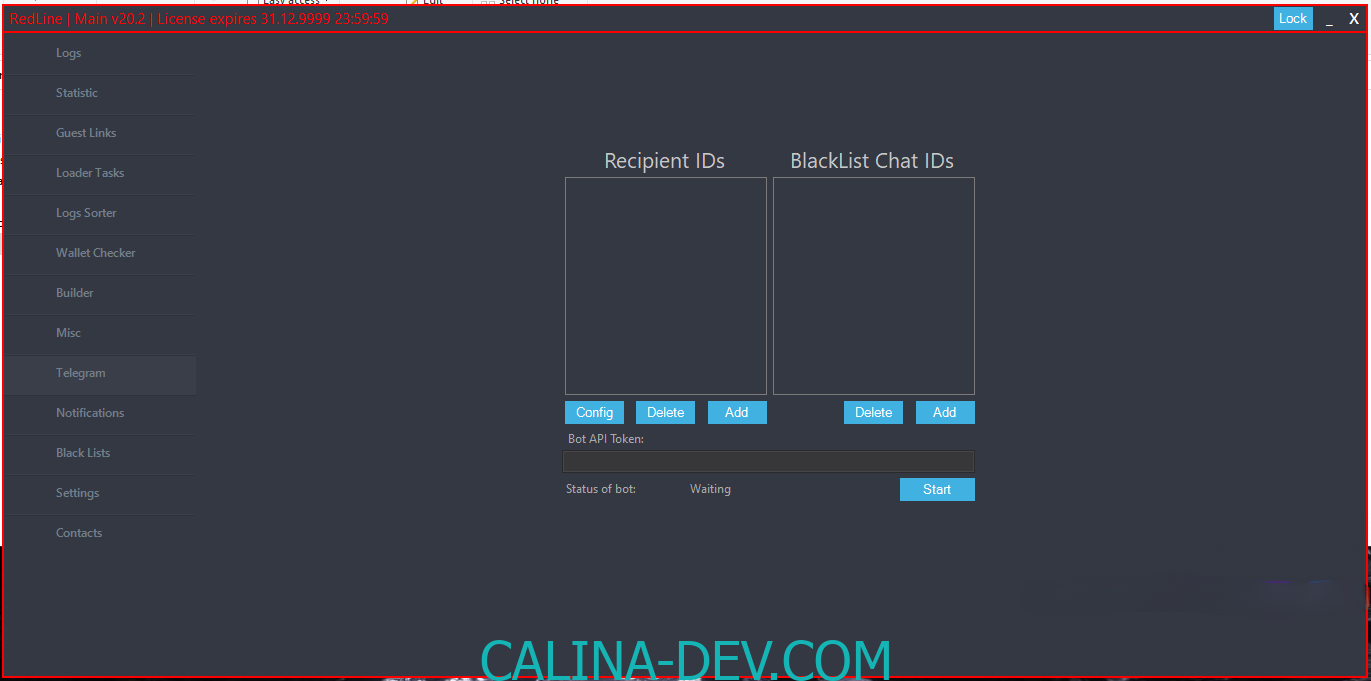
- Desktop Applications:
RedLine Stealer exhibits a particular interest in three desktop programs: Discord, Steam, and Telegram Messenger. Its primary objective is session hijacking and the theft of session-related files. While Discord and Steam use similar session management methods based on tokens, RedLine Stealer scans their directories in AppData, searching for session tokens by adhering to specific naming conventions. In the case of Telegram, which employs a different mechanism for session handling, RedLine Stealer seizes all possible files related to the user session stored in the AppDataTelegram Desktoptdata folder.
- VPN and FTP Applications:
RedLine Stealer is also capable of harvesting login credentials from various VPN services and FTP applications. Notable targets include OpenVPN, NordVPN, ProtonVPN, and FileZilla. The stealer’s approach is straightforward – it searches for configuration files in the user directories of these applications. For example, in the case of NordVPN, it seeks out.config files within the AppDataLocalNordVPN directory, specifically focusing on nodes “//setting/vvalue.”
Conclusion
RedLine Data Stealer’s multifaceted capabilities and relentless pursuit of sensitive information pose a considerable threat to cybersecurity. Understanding its modus operandi is vital in fortifying defenses against this insidious adversary. As the landscape of cyber threats continues to evolve, staying vigilant and informed is essential in safeguarding digital assets and sensitive data.
PASSWORD : calina-dev.com

Password : calina-dev.com
We Love Cricket
We Love Cricket








Leave a Reply